Protect Your Privacy Online: 5 Smart Moves to Stay Safe in 2025
Dr. Simeon Olaomo
3 min read


Online privacy is no longer a nice‑to‑have feature; it’s a baseline requirement for anyone who spends time on the internet. Hidden trackers, AI‑driven profiling, and pervasive data collection mean that every click can be logged, analyzed, and sold. Fortunately, you don’t need a degree in cybersecurity to defend yourself. By adopting a handful of proven tools and disciplined habits, you can dramatically limit the amount of personal information that leaves your device.
1. Choose a Privacy‑First Browser
The browser is the gateway through which most tracking occurs. Replace default browsers with ones that block ads, trackers, and fingerprinting out of the box.
BrowserWhy It Works
- Brave: Built‑in ad and tracker blocking, HTTPS‑only mode, optional Tor tab for extra anonymity.
- Mozilla Firefox (hardened): Enables strict tracking protection by default; add uBlock Origin and
Privacy Badger for layered defense.
- DuckDuckGo Privacy Browser (mobile)Auto‑blocks hidden trackers and forces encrypted connections where possible.
Additional steps
Disable third‑party cookies in the browser settings.
Use container tabs (e.g., Firefox Facebook Container) to isolate social‑media sessions from the rest of your browsing activity.
2. Route All Traffic Through an Encrypted VPN
A Virtual Private Network encrypts the data leaving your device, masks your IP address, and prevents ISPs, malicious apps, or network operators from observing your activity.
VPNKey Characteristics
Mullvad No email required, accepts anonymous payments, publishes full audit reports.
Proton VPN Swiss jurisdiction, strong AES‑256 encryption, free tier with limited servers.
IVPN Zero‑log policy, multihop routing, built‑in anti‑tracking features.
Avoid free VPN services that monetize by selling browsing data or that operate under jurisdictions with mandatory data retention laws. Install the VPN client on every device you own—including smartphones, tablets, and IoT gadgets—to ensure consistent coverage.
3. Secure Email and Search Habits
Your email provider and search engine are two of the most valuable data sources for advertisers and threat actors.
ProtonMail – End‑to‑end encryption, hosted in privacy‑friendly Switzerland.
Tutanota – Open‑source, encrypted by default, no ads.
Search
DuckDuckGo – No user profiling, does not store query logs.
Startpage – Retrieves Google results while stripping identifying information.
Alias Management
Create disposable email addresses with services like SimpleLogin or Firefox Relay. Use these aliases when signing up for newsletters, promotions, or any site that does not require your primary address.
4. Harden Social‑Media Presence
Even private accounts can leak data through metadata, friend‑of‑friend visibility, and platform‑wide tracking.
Set every profile (Facebook, Instagram, X/Twitter, TikTok, LinkedIn) to private wherever the option exists.
Turn off location services and avoid posting real‑time geotags.
Use pseudonyms or separate handles for non‑professional interactions.
Regularly audit permissions granted to third‑party apps.
Helpful Tools
Jumbo Privacy – Scans social accounts and highlights overshared data, offering one‑click remediation.
Firefox Facebook Container – Isolates Facebook’s tracking cookies from the rest of your browsing session.
5. Adopt Robust Authentication Practices
Credential reuse is the single biggest factor behind most data breaches. Strengthening passwords and adding a second verification factor dramatically reduces risk.
Generate a unique, high‑entropy password for every service.
Store them securely in a reputable password manager:
Bitwarden – Open‑source, free tier includes secure cloud sync.
1Password – User‑friendly, supports families and teams.
Enable Two‑Factor Authentication (2FA) on all critical accounts. Prefer authenticator apps (Authy, Aegis) or hardware tokens (YubiKey) over SMS‑based codes.
6. Keep Software Updated and Minimize Attack Surface
Apply operating‑system, browser, and application updates promptly; patches often address active exploits.
Disable or uninstall unnecessary plugins, extensions, and background services.
Use a reputable endpoint protection suite that focuses on exploit mitigation rather than intrusive advertising.
7. Practice Data Minimization
Ask yourself before you share: Is this information necessary? Limit the amount of personal data you provide to online forms, and delete old accounts you no longer use. When possible, opt for services that collect the least amount of data by design.
Closing Thoughts
Privacy in 2025 is less about hiding and more about exercising control over your digital footprint. By selecting privacy‑centric browsers, encrypting all traffic with a trustworthy VPN, securing email and search, tightening social‑media settings, and enforcing strong authentication, you create a layered defense that thwarts most commercial and governmental tracking attempts.
Adopt these practices as part of your everyday routine, review them periodically, and stay informed about emerging threats. With disciplined use of the tools outlined above, you can navigate the modern internet confidently, knowing that your personal data remains largely under your own command.
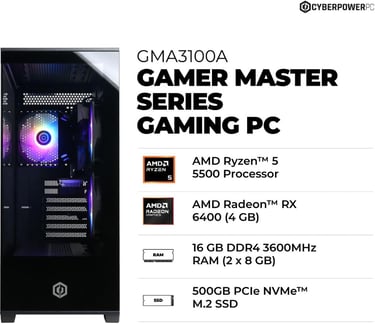
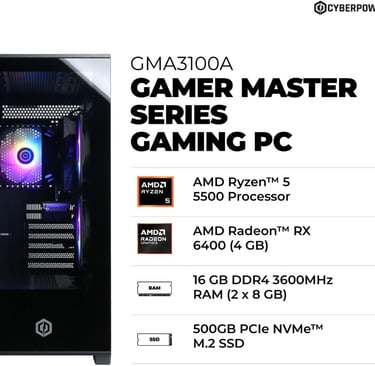
CyberPowerPC Gamer Master Gaming PC, AMD Ryzen 5 5500 3.6GHz, Radeon RX 6400 4GB, 16GB DDR4, 500GB PCIe Gen4 SSD, WiFi Ready & Windows 11 Home (GMA3100A)



