Cybersecurity Outlook 2026: Top 10 Emerging Threats Every Organization Must Prepare For
TECHUPSCALE
13 min read




Cybersecurity is evolving at a rapid pace. As we approach 2026, the landscape of cyber threats is becoming more complex. Organizations must stay vigilant to protect their digital assets.
Emerging technologies are reshaping the tactics used by cybercriminals. AI and machine learning are now tools for both defense and attack. This dual use presents new challenges for security teams.
The Internet of Things (IoT) is expanding, creating more entry points for cyber attacks. Each connected device is a potential vulnerability. Securing these devices is crucial for maintaining network integrity.
Ransomware continues to evolve, with new tactics like double extortion gaining traction. Attackers are becoming more sophisticated, demanding higher ransoms. Organizations need robust strategies to counter these threats.
Supply chain attacks are on the rise, targeting weaker links to infiltrate larger networks. This trend highlights the importance of comprehensive security measures. Protecting the entire supply chain is essential.
Deepfake technology is another emerging threat, used for identity theft and misinformation. As this technology advances, it becomes harder to detect. Vigilance and advanced detection tools are necessary.
State-sponsored cyber attacks are increasing, driven by geopolitical tensions. These attacks are often sophisticated and targeted. Organizations must be prepared for these high-level threats.
Remote work has expanded the attack surface, making security more challenging. Ensuring secure remote access is now a priority. Zero-trust architecture can help mitigate these risks.
In this article, we explore the top 10 emerging cyber threats of 2026. Understanding these threats is the first step in building a resilient defense. Prepare now to safeguard your organization’s future.
The Evolving Cyber Threat Landscape: What’s Changing by 2026?
By 2026, cyber threats will be more advanced than ever. This evolution is driven by rapid technological advancements. Organizations must anticipate these changes to stay ahead.
AI and machine learning will be at the forefront of cyber attacks. These technologies allow for more targeted and efficient breaches. Cybercriminals will use AI to automate complex attacks.
The growth of IoT devices significantly increases the risk of vulnerabilities. These devices often lack robust security measures. Hackers are likely to exploit these weaknesses more frequently.
In ransomware, new methodologies like double extortion will become common. Attackers not only encrypt data but also threaten to release it. This evolution demands new defense tactics.
Supply chain attacks will continue to grow. Cybercriminals will target the least secure elements. Effective strategies must address these threats at every point of the chain.
Deepfake and synthetic media technologies will revolutionize misinformation campaigns. The difficulty in distinguishing real from fake will increase. Organizations need to develop sophisticated detection capabilities.
The key trends expected by 2026 include:
AI-Driven Breaches: Automated and highly targeted attacks.
IoT Vulnerabilities: Exploiting weak security in connected devices.
Ransomware Evolution: Adoption of double extortion tactics.
Supply Chain Threats: Attacking weaker links to breach larger entities.
Deepfake Proliferation: Advanced identity and misinformation attacks.
The geopolitical landscape will further complicate cybersecurity. State-sponsored actors will increase in sophistication and frequency. These threats require concerted defense efforts.
Remote work will continue to expand the attack surface. Ensuring secure operations from anywhere is critical. Zero-trust and continuous monitoring will be essential strategies.
Organizations should prioritize adaptive and proactive security measures. The future will require agility in response to rapidly changing threats. Preparing now will ensure resilience against cyber adversities.
1. AI-Driven Cyber Attacks: Automation and Sophistication at Scale
The rise of AI is reshaping cybersecurity. By 2026, cybercriminals will leverage AI to enhance their attacks. This approach allows them to conduct operations at an unprecedented scale and precision.
AI's strength lies in its ability to learn and adapt. It processes vast data to develop strategies, making attacks unpredictable. Such adaptability poses significant challenges for traditional defense mechanisms.
One of the primary uses of AI in cybercrime is automation. AI can automate repetitive tasks, freeing attackers to focus on high-value targets. This capability increases the volume and speed of attacks.
Moreover, AI can identify vulnerabilities faster than human analysts. It scans systems continuously, learning from failures to improve its strategies. Consequently, security teams must rethink their defense strategies.
Organizations face the threat of AI-generated phishing attacks. These attacks can mimic legitimate communications almost flawlessly. As these methods evolve, they're harder to detect without advanced tools.
Key concerns about AI-driven cyber attacks by 2026 include:
Scalability: Attacks can target many systems simultaneously.
Adaptability: AI continuously modifies its techniques for better efficacy.
Automation: Increases attack frequency and reduces operational overhead.
Intelligent Phishing: Crafting personalized and believable phishing emails.
To combat AI-driven threats, organizations must embrace AI in their defense strategies. AI-enhanced security tools can provide automated monitoring and response. They can identify anomalous activities in real-time, offering a critical edge.
Moreover, fostering an AI-aware culture is essential. Companies should educate employees about these new threats. This education will enhance awareness and preparedness against sophisticated attacks.
In summary, the integration of AI in cybercrime heightens both opportunity and danger. As AI evolves, so too must our defenses. Preparing for these sophisticated attacks will be a vital component of cybersecurity strategies by 2026.
2. Deepfake Technology and Synthetic Identity Threats
In the digital age, deepfakes represent a growing threat by 2026. These sophisticated forgeries use AI to create highly realistic fake audio and video. Cybercriminals leverage this technology to advance fraud and deception.
Deepfakes have the potential to disrupt both personal and professional spheres. In corporate settings, they could be used to impersonate executives, leading to financial fraud. This creates an urgent need for robust verification processes.
Moreover, deepfake technology enables synthetic identity fraud. Cybercriminals generate identities that don’t exist, exploiting them to open fraudulent accounts. These fake identities are difficult to detect, bypassing traditional security measures.
Deepfakes also threaten information integrity. They can be used to discredit individuals or spread misinformation. This misuse can manipulate public opinion or undermine trust in media outlets.
Key vulnerabilities associated with deepfake and synthetic identity threats include:
Impersonation: Pretending to be someone else to carry out scams.
Fraudulent Transactions: Conducting financial fraud through synthetic identities.
Misinformation: Spreading false information to manipulate public perceptions.
Reputation Damage: Utilizing fake media to damage individuals' or brands' reputations.
Combating these threats requires a multi-faceted approach. Detection technologies must evolve to identify anomalies in digital media. Solutions include deploying AI algorithms designed to spot deepfakes early.
Organizations should also focus on educating employees about these new threats. Awareness programs can improve skepticism towards unsolicited requests and unverified content. As technology evolves, vigilance will remain crucial in maintaining digital trust.
In conclusion, as deepfake and synthetic identity threats grow, organizations must adapt their strategies. Only by staying ahead of these deceptive technologies can they safeguard their assets and reputation effectively.
3. Ransomware Evolution: Double Extortion and Ransomware-as-a-Service
Ransomware is rapidly becoming more sophisticated. By 2026, we'll see significant innovations in this cyber threat. Criminals are enhancing their tactics to extract maximum value from victims.
Double extortion is a prime example of this evolution. Attackers not only encrypt victim data but also threaten to leak it. This creates additional pressure on victims to pay quickly.
Moreover, the advent of Ransomware-as-a-Service (RaaS) democratizes cybercrime. It allows even low-skilled hackers to deploy sophisticated attacks. This model makes ransomware more accessible and increases its prevalence.
As a result, organizations face multiple risks. Financial losses can be immense, and reputational damage is a lingering threat. Recovery from ransomware attacks often involves both monetary payment and reputational management.
Key characteristics of these emerging threats include:
Double Extortion: Using data leakage threats to increase pressure on victims.
Monetization via RaaS: Enabling widespread ransomware deployment by enabling non-expert hackers.
Extensive Damage: Disruptions lead to substantial financial and operational losses.
Reputational Harm: Public exposure of breaches causes long-term reputation challenges.
To mitigate these risks, organizations need robust backup strategies. Regularly updated and secure data backups can minimize the impact of a ransomware event. In addition, incident response plans should be in place to handle these situations effectively.
Moreover, organizations should enhance their preventive measures. This includes implementing advanced endpoint protections and threat detection systems. Employee education is also crucial in preventing unauthorized access and phishing attacks, often precursors to ransomware incidents.
By investing in comprehensive security strategies, organizations can better defend against the evolving landscape of ransomware threats. In this ever-changing cyber realm, preparation and adaptability remain key.
4. Supply Chain Attacks: Weakest Link Exploitation
Supply chain attacks are becoming a central concern for cybersecurity by 2026. These attacks exploit vulnerabilities in an organization's extended network. Instead of targeting well-guarded systems directly, attackers infiltrate through less secure suppliers.
This tactic proves highly effective. Suppliers often lack robust security measures, providing attackers a gateway. Once inside, cybercriminals can inflict damage on the primary organization. The ripple effects of such breaches can extend far beyond initial intrusion points.
Supply chain vulnerabilities are numerous. Organizations often integrate complex vendor ecosystems, each with its own security standards. This complexity makes it challenging to monitor and secure every link. Attackers capitalize on this opacity to implant malicious software undetected.
Key aspects of supply chain attacks include:
Third-Party Risks: Vendors with weak security can become targets.
Network Complexity: Managing multiple third-party relationships makes unified security challenging.
Data Breach Potential: Data shared among suppliers can be intercepted or altered.
Integration Gaps: Various software platforms interacting can create unforeseen vulnerabilities.
To combat these threats, organizations must prioritize supply chain security. A comprehensive audit of supplier security protocols should be undertaken regularly. Establishing stringent criteria for vendor partnerships is also essential to protect sensitive data.
Moreover, visibility across the entire supply chain should be enhanced. Organizations should adopt technologies that provide real-time monitoring of supplier interactions. This foresight can aid in early detection of irregular activities.
Investing in stronger collaborative defenses, such as shared threat intelligence with partners, can also fortify defenses against supply chain attacks. By understanding and securing supply chain vulnerabilities, businesses can sustain operational integrity and protect critical assets.
5. Quantum Computing: The Encryption Arms Race
Quantum computing is set to revolutionize technology by 2026. With its immense computational power, it poses both opportunities and threats. This technology can solve complex problems much faster than current computers, advancing fields like science and medicine.
However, the impact on cybersecurity is significant. Quantum computers could potentially break current encryption methods. Methods like RSA and ECC, which secure data today, might become obsolete. This capability threatens everything from financial transactions to personal data security.
Organizations worldwide are now racing to develop quantum-resistant encryption. Governments and private sectors are heavily investing in research. The goal is to create cryptographic systems that withstand quantum attacks. This is crucial for maintaining data confidentiality and integrity.
Here are key areas affected by quantum computing:
Data Encryption: Traditional encryption methods are at risk.
Public Key Infrastructure: Systems could be compromised by powerful decryption capabilities.
Cyber Defense Strategies: New approaches are required to ensure data remains secure.
Emerging Standards: Development of quantum-safe algorithms is underway.
Preparation for this encryption challenge is essential for organizations. Exploring quantum-safe cryptography and integrating these solutions proactively can mitigate risks. By adapting early to quantum developments, businesses can maintain secure environments and protect sensitive data from future threats. Conclusively, although quantum computing presents challenges, it also inspires innovation in cybersecurity strategies.
6. IoT and Smart Infrastructure Vulnerabilities
By 2026, the proliferation of IoT devices will reach unprecedented levels. From smart homes to connected cities, IoT is transforming daily life. However, these interconnected devices often come with significant security risks. Many IoT devices are developed with convenience in mind, often at the expense of robust security measures.
As more devices connect to networks, they expand the attack surface available to cybercriminals. Vulnerabilities in IoT devices can provide hackers with an entry point into larger systems, potentially leading to severe breaches. Threats range from hijacking devices to launching large-scale attacks.
A significant concern is the security of critical infrastructure. Power grids, transportation systems, and healthcare facilities are increasingly IoT-dependent. Compromising these networks can disrupt services and cause widespread damage.
Some key areas of focus for addressing IoT vulnerabilities include:
Device Security: Ensuring devices have up-to-date firmware and encryption.
Network Segmentation: Isolating IoT devices from sensitive networks to limit access.
Vendor Standards: Encouraging manufacturers to adhere to strict security guidelines.
Organizations need to prioritize securing these devices to prevent exploitation. Implementing comprehensive security protocols and vendor assessments will be crucial. As IoT technology evolves, maintaining security vigilance will ensure continued growth without compromising safety. Balancing innovation with security in IoT will be a defining challenge for the coming years.
7. Insider Threats and Shadow IT: The Enemy Within
Insider threats are becoming more sophisticated, presenting a serious risk by 2026. Employees, whether negligent or malicious, can compromise security unintentionally or intentionally. Insider threats are challenging because they involve people with legitimate access to an organization's systems.
Shadow IT adds complexity to the insider threat landscape. Employees often use unauthorized devices and applications to boost productivity. While this can be beneficial, it bypasses corporate security measures, increasing vulnerability.
Unchecked, shadow IT can lead to data breaches. It enables the storage and transfer of sensitive information without oversight. This lack of control can quickly escalate into major security incidents.
To mitigate these threats, organizations should focus on:
Education and Awareness: Regular training on security protocols and policies.
Access Management: Implementing strict access controls and monitoring.
Shadow IT Detection: Using tools to identify and manage unauthorized applications.
Balancing accessibility and security in the workplace is vital. Encouraging a culture of compliance and awareness can reduce insider threats significantly. Proactive measures are essential to protect against the risks posed by trusted individuals. As technology evolves, insider threat detection and management must keep pace to safeguard sensitive information.
8. Cloud Security Gaps and Data Breaches
Cloud computing has revolutionized business operations, providing flexibility and scalability. However, with these benefits come unique security challenges. As organizations increasingly migrate data to the cloud, they face various risks associated with cloud environments.
Misconfigured cloud services remain a significant vulnerability. Incorrect settings can expose sensitive data, leaving it accessible to unauthorized users. Misconfigurations often occur due to human error or insufficient understanding of cloud security protocols.
Data breaches in the cloud can have severe financial and reputational consequences. The lack of clear visibility into cloud environments complicates incident detection and response efforts. Companies must adopt robust strategies to monitor and secure cloud applications effectively.
Key measures to address cloud security gaps include:
Regular Audits: Assess cloud configurations and access controls routinely.
Encryption: Protect data both at rest and in transit.
Continuous Monitoring: Employ tools to detect suspicious activities in real-time.
Cloud providers often offer built-in security features that organizations may underutilize. Leveraging these tools can bolster defenses against data breaches. A proactive approach to cloud security will ensure that the advantages of cloud computing are not undermined by potential vulnerabilities. As cloud adoption grows, so does the need for comprehensive security frameworks to protect vital data assets.
9. State-Sponsored and Geopolitical Cyber Attacks
State-sponsored cyber attacks are increasingly prominent, driven by geopolitical tensions and national interests. These attacks typically aim to destabilize economies, disrupt services, or gain strategic intelligence.
Such attacks are characterized by their sophistication and resources. State actors employ advanced persistent threats (APTs) that can infiltrate networks and remain undetected for long periods. These threats can target critical infrastructure, highlighting the intersection of cybersecurity and national security.
Common tactics used by state-sponsored cyber attackers include:
Phishing and Spear Phishing: Deceptive techniques to gain sensitive information.
Malware Deployment: Using malicious software to sabotage or extract data.
Supply Chain Exploits: Compromising less secure third-party systems to infiltrate primary targets.
Organizations need to enhance their threat intelligence capabilities to anticipate and mitigate these threats. Collaboration with government agencies can provide vital insights and resources. Implementing strict cybersecurity policies and fostering a culture of awareness are crucial in defending against these sophisticated attacks. As geopolitical instability persists, businesses and governments must remain vigilant and prepared to counteract state-sponsored digital threats. This proactive stance is essential to safeguard national interests and maintain operational integrity.
10. Social Engineering and Human Factor Exploitation
Cybercriminals recognize humans as the weakest link in cybersecurity. Social engineering attacks exploit human psychology, manipulating individuals into divulging confidential information or granting unauthorized access.
These attacks take various forms and leverage trust, fear, or urgency to achieve their objectives. Phishing remains the most prevalent method, using deceptive emails to trick recipients into revealing data or clicking malicious links. Sophisticated versions, such as spear phishing, are even more tailored and convincing.
Other common social engineering tactics include:
Pretexting: Fabricating scenarios to obtain sensitive data.
Baiting: Enticing victims with false promises to compromise systems.
Vishing (Voice Phishing): Using phone calls to elicit information.
Organizations must prioritize awareness and education to combat these threats. Regular training programs can equip employees with the skills to recognize and respond to suspicious activities. Implementing robust security protocols, like multi-factor authentication, adds layers of protection against successful exploits. As social engineering techniques evolve, staying informed and vigilant is crucial. By understanding how cybercriminals target individuals, organizations can better safeguard their assets and maintain security posture.
Proactive Defense: Strategies to Mitigate 2026’s Top Cyber Security Risks
Navigating the evolving landscape of cyber threats demands preemptive and adaptive strategies. Organizations must develop robust defenses to counteract the anticipated risks of 2026.
A crucial starting point is implementing a zero-trust architecture. This approach assumes that threats exist both inside and outside the network, minimizing risk by limiting access and continuously verifying user identities.
Investments in AI-driven threat detection can significantly enhance an organization’s capability to identify anomalies and respond swiftly to potential breaches. These technologies enable automated defenses, reducing response times and mitigating damage.
Creating a culture of security awareness is equally important. Regular training sessions should empower employees to recognize threats, fostering a proactive security culture. Enabling employees with the knowledge to identify phishing attempts or suspicious behaviors can thwart many attacks.
Collaboration is vital in staying ahead. Sharing threat intelligence across industries helps organizations identify emerging threats faster. Partnerships with cybersecurity firms and participation in information-sharing platforms can enrich security protocols.
Comprehensive incident response plans ensure that organizations can respond effectively to breaches, minimizing downtime and financial impact. Regular drills and updates to these plans enhance preparedness.
Key strategies include:
Zero-Trust Model: Implement stringent access controls and continuous monitoring.
AI and Automation: Utilize AI for anomaly detection and quick responses.
Additional steps encompass:
Employee Training: Conduct regular cybersecurity awareness programs.
Incident Response: Develop and maintain comprehensive response protocols.
By embracing these proactive measures, organizations can strengthen their defense against future cyber threats, safeguarding their operations and maintaining trust in an increasingly digital world.
Building a Resilient Organization: Policy, Culture, and Technology
Resilience in cybersecurity requires harmonizing policy, culture, and technology. Organizations must foster an environment where security is intrinsic to their operations.
Establishing comprehensive cybersecurity policies is vital. These policies should align with regulatory standards and industry best practices. Regular audits ensure compliance and identify areas for improvement, keeping the organization in line with evolving threats.
Creating a security-focused organizational culture is equally important. Leaders should champion cybersecurity from the top, instilling its importance in every employee. A culture that values and rewards proactive threat identification fosters a vigilant workforce.
Technology investments also play a crucial role. Leveraging cutting-edge cybersecurity tools fortifies defenses. Technologies like encryption, multi-factor authentication, and intrusion detection systems are foundational elements.
In summary, key components to build resilience include:
Policy Alignment: Ensure all policies meet or exceed standards.
Cultural Commitment: Develop a security-first mindset across all levels.
Technological Integration: Deploy advanced security tools and infrastructure.
By intertwining strong policies, a culture of security, and innovative technology, organizations can better withstand and recover from cybersecurity challenges. Such a holistic approach not only protects assets but also preserves organizational reputation and customer trust.
Conclusion: Preparing for the Future of Cyber Crime Trends
As we look towards 2026, the landscape of cybercrime will likely become more complex and sophisticated. Organizations must proactively gear up for these evolving threats to safeguard their assets.
Adopting advanced cybersecurity measures is critical. Staying informed about emerging trends, like AI-driven attacks and ransomware-as-a-service, will be essential for effective defense strategies. Anticipating these threats allows for better preparation and response.
Building organizational resilience should be a continuous effort. Strong policies, a culture of awareness, and cutting-edge technology form the backbone of a robust defense. By investing in these areas, organizations not only protect themselves but also strengthen their position in an ever-changing cyber environment.
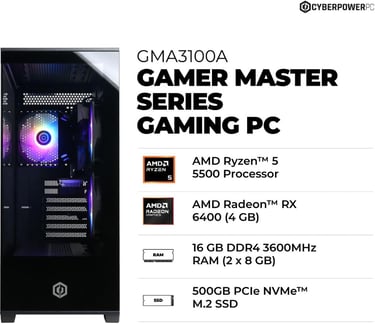
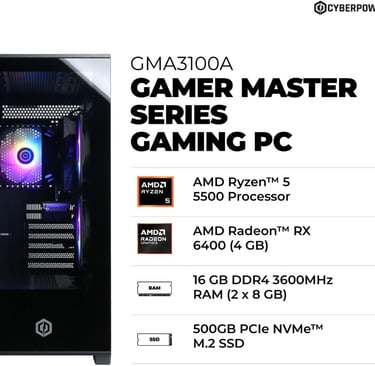
CyberPowerPC Gamer Master Gaming PC, AMD Ryzen 5 5500 3.6GHz, Radeon RX 6400 4GB, 16GB DDR4, 500GB PCIe Gen4 SSD, WiFi Ready & Windows 11 Home (GMA3100A)



